
by Daniel Ruiz
Practice Lead, Citrix Technologies
Citrix announced new vulnerabilities discovered in Citrix ADM that could result in the following security issues.
- Corruption of the system by a remote, unauthenticated user. The impact of this can include the reset of the administrator password at the next device reboot, allowing an attacker with SSH access to connect with the default administrator credentials after the device has rebooted.
- Temporary disruption of the ADM license service. The impact of this includes preventing new licenses from being issued or renewed by Citrix ADM.
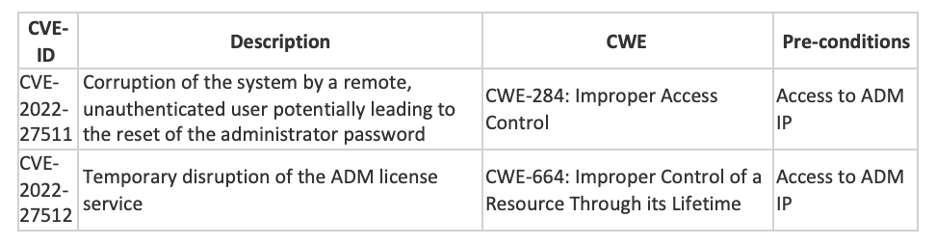
All supported versions of the Citrix ADM server and Citrix ADM agent are affected by this vulnerability.
Affected Citrix ADM builds:
- Citrix ADM 13.1 before 13.1-21.53
- Citrix ADM 13.0 before 13.0-85.19
- Please note that Citrix ADM 12.1 has now reached End of Life and is no longer supported. Customers running Citrix ADM 12.1 are recommended to upgrade to a supported version as soon as possible.
For Citrix Cloud ADM customers, these vulnerabilities have already been addressed in the Citrix Cloud ADM service.
Customers using the Citrix Cloud ADM service do not need to take any action.
Solution:
Citrix recommends that affected customers install the relevant updated versions of the Citrix ADM server and Citrix ADM agent as soon as possible:
- Citrix ADM 13.1-21.53 and later versions of 13.1
- Citrix ADM 13.0-85.19 and later versions of 13.0
- Customers must upgrade the Citrix ADM server and all associated Citrix ADM agents.
If you would like more information or assistance from our industry leading team of Citrix experts to plan and execute the upgrade, please contact us at service@helient.com.


