Citrix Announces New Vulnerabilities in Citrix ADC & Citrix Gateway (NetScalers)
 by Daniel Ruiz
by Daniel Ruiz
Practice Lead, Citrix Technologies
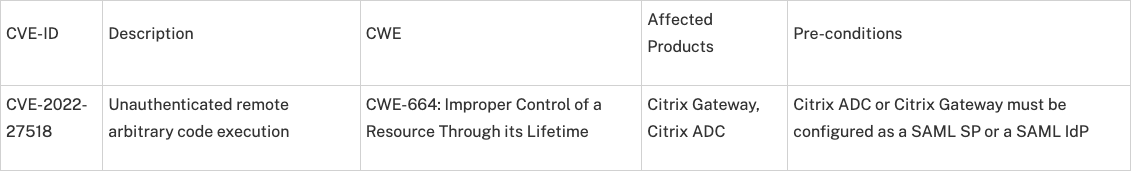
Citrix announced new vulnerabilities discovered in Citrix ADC and Citrix Gateway. These vulnerabilities have the following identifiers:
Affected versions of Citrix ADC and Citrix Gateway: (Citrix ADC and Citrix Gateway version 13.1 is unaffected.)
- Citrix ADC and Citrix Gateway 13.0 before 13.0-58.32
- Citrix ADC and Citrix Gateway 12.1 before 12.1-65.25
- Citrix ADC 12.1-FIPS before 12.1-55.291
- Citrix ADC 12.1-NDcPP before 12.1-55.291
Review:
To determine if their Citrix ADC or Citrix Gateway is configured as a SAML SP or a SAML, review the ns.conf file located under /flash/nsconfig.
To view the ns.conf file via an FTP client:
- Connect to the source system via WinSCP
- Review the ns.conf file and look for
- add authentication samlAction (indicates the appliance is configured as a SAML SP)
OR
- add authentication samlIdPProfile (indicates the appliance is configured as a SAML IdP)
To review via command line:
- Connect to the source system via Putty
- Type:
sh run | grep samlAction
sh run | grep samlIdPProfile
Solution:
Citrix recommends that affected customers install the relevant updated versions of Citrix ADC or Citrix Gateway as soon as possible.
- Citrix ADC and Citrix Gateway 13.0-58.32 and later releases
- Citrix ADC and Citrix Gateway 12.1-65.25 and later releases of 12.1
- Citrix ADC 12.1-FIPS 12.1-55.291 and later releases of 12.1-FIPS
- Citrix ADC 12.1-NDcPP 12.1-55.291 and later releases of 12.1-NDcPP
If you would like more information or assistance from our industry leading team of Citrix experts to plan and execute the upgrade, please contact us at service@helient.com.