Recently Discovered Vulnerabilities With Some Email Clients Using S/MIME or PGP Encryption
 by Michael Bianchi, Senior Systems Engineer
by Michael Bianchi, Senior Systems Engineer
Yesterday, security researchers published information about flaws discovered with some clients using S/MIME or PGP for end-to-end email encryption. These technologies add a layer of security to emails in addition to TLS which prevents attackers from compromising the contents of emails even if they have access to them from the client or server side.
There are currently no patches for this vulnerability, but a work around involves having all parties in an email chain/thread disable viewing of HTML encoded emails in their respective client. If even one participant in the email chain is vulnerable, the email may be subject to this vulnerability.
All versions of Outlook as well as Apple and Android mail apps using S/MIME are currently vulnerable. Outlook 2010, 2013 and 2016 are not vulnerable if using PGP. See below table for which clients are confirmed affected:
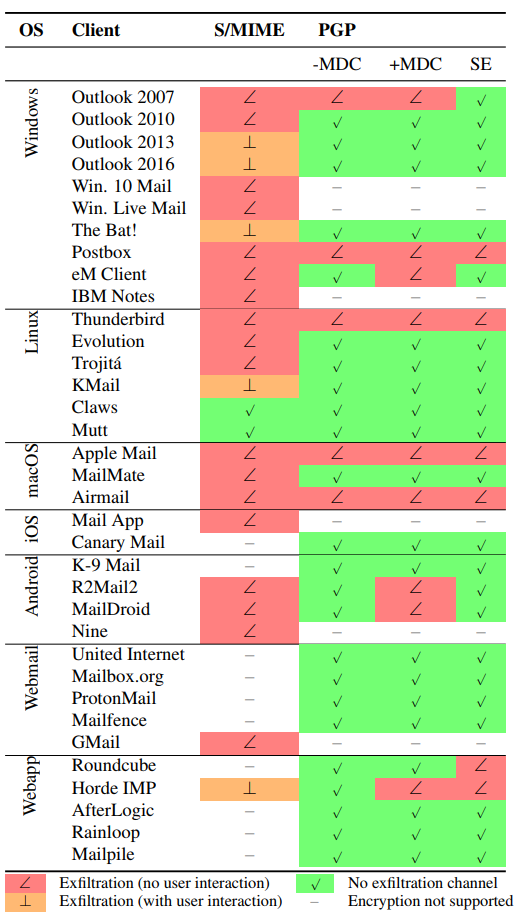
Patches should be forthcoming for all affected applications that are under support. NOTE: Outlook 2007 is out of support and will not be patched. If you use one of the affected clients and rely on end-to-end encryption being guaranteed due to compliance, consider using other forms of communication in the interim.
For more information, Helient is here to assist at service@helient.com.
